Deep Packet Analysis
as part of service Monitoring
- all protocols – all layers -all IT services
- deepest level into Service KPIs
- data for secunds – up to years
Deep Packet Analysis for PCAP Files, long time monitoring with user defined protocol metrics.
SharkMon
WHY SHARKMON
USPs
- packet data anywhere – import 10000s of pcap files
- from differnt datasources
- deepest and widest packet monitoring in the industry
- covering all IT communication layers – routing analysis, WIFI, Telco, Quik, DNS, NTP, Radius, VoIP, Industrial data, SMB, HTTP/s, TLS …
- auto-analysis of packet data
- indexing of metrics , sessions, technologies
- export data for service management
use cases
- Service providers, Telcos
- industrial manufacturing
- data center
- routing / WLAN /VoIP monitoring
- cloud service monitoring
- Security Analysis
- Service Performance & Availability
- Service Monitoring and SLA
Input
Sharkmon imports network packet data into PCAP files from distributed data sources (Capture Appliances , Servers, firewalls, cloud systems , user PC, agents).
Sharkmon can also access capture appliances via API that import and process raw network data.
Sharkmon can run as instance in the private cloud, in data center – or as VM on your local PC
Sharkmon analyzes packet data based on freely definable profiles, which can contain all protocols and their fields that can be identified in Shark.
Sharkmon is based on a versatile analysis concept, which means critical conditions can be precisely identified.
Threshold values can be stored to enable the identification of critical values and to recognize and forward incidents.
Processing
Output
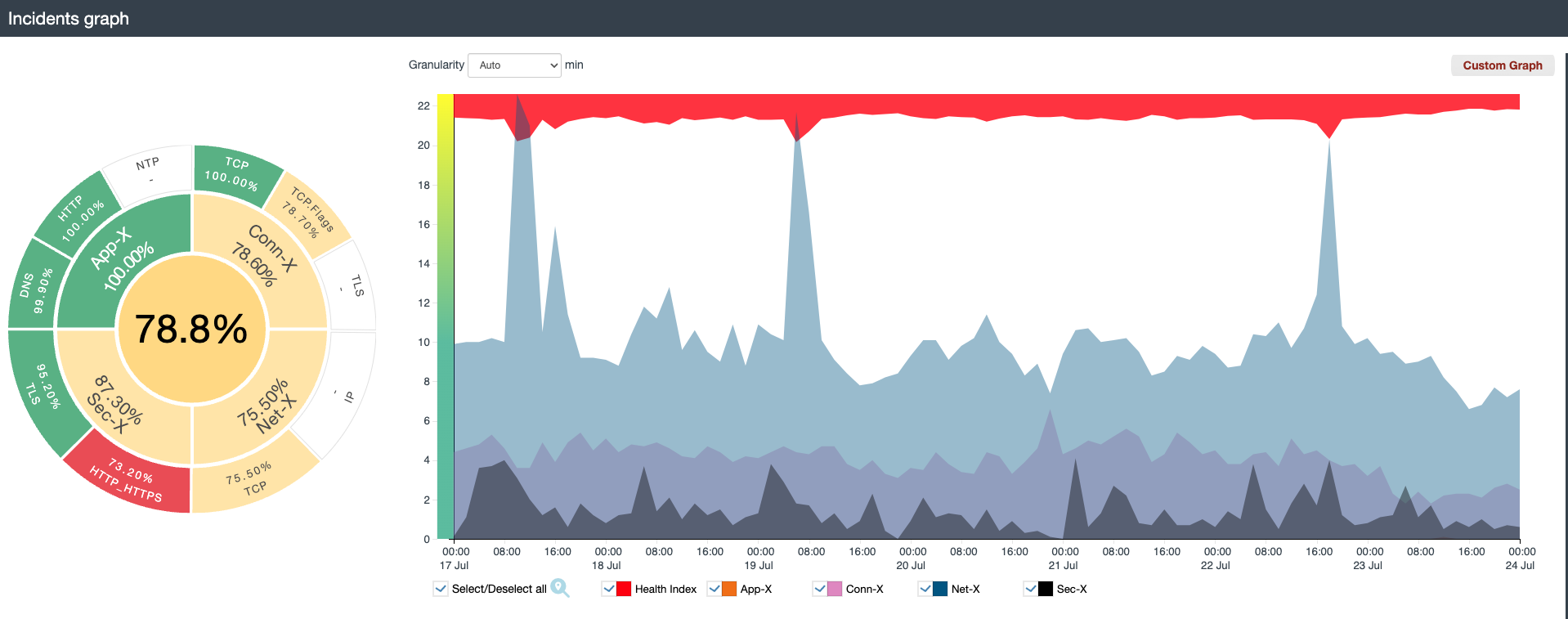
Sharkmon presents the data in web-based top-down dashboards that allow the presentation of months, hours or seconds.
Sharkmon values and incidents can be exported and correlated with other data from other monitoring solutions (such as system/network management, support tickets, etc.) in our KPI platform SLIC.
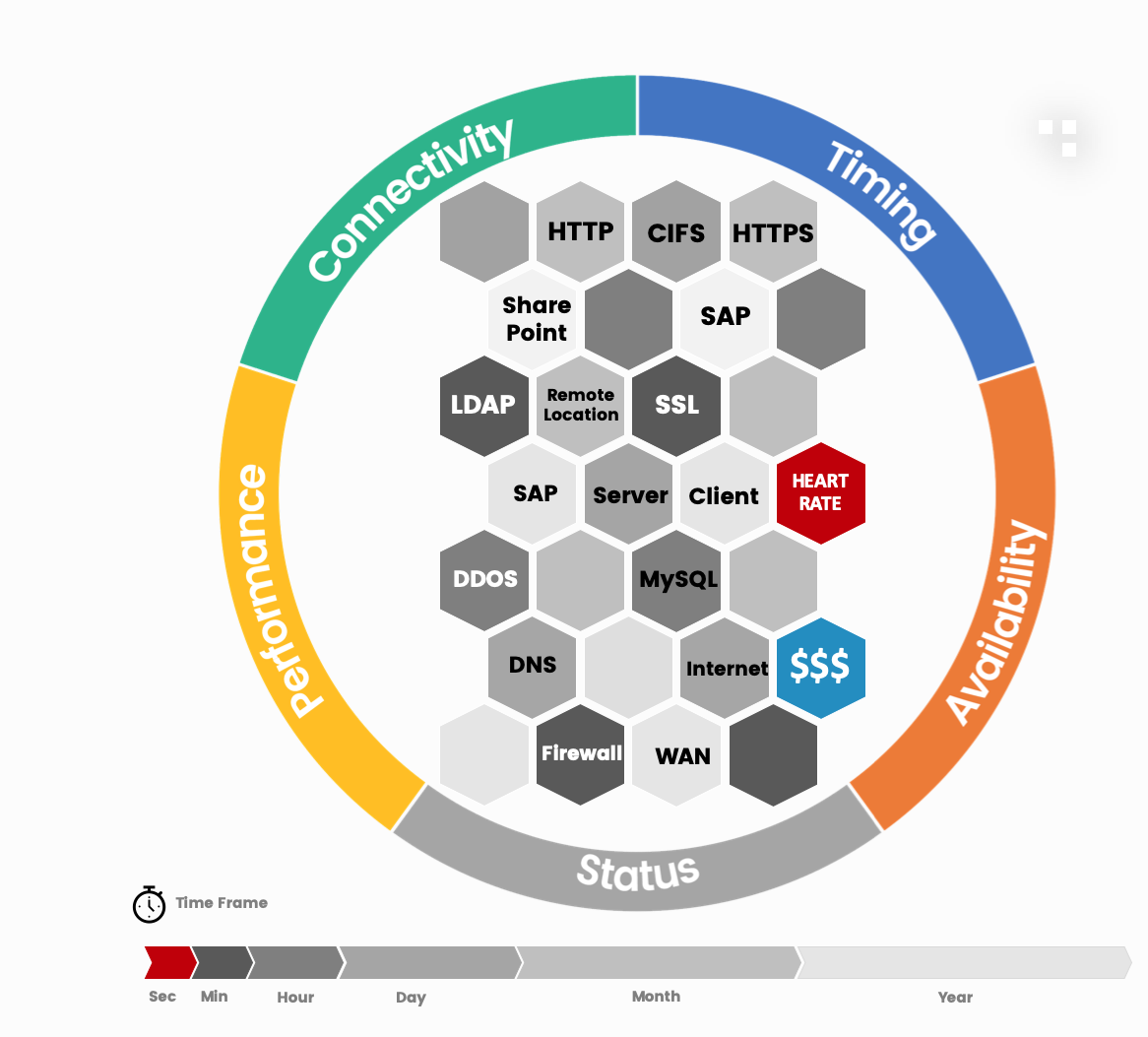
Features
- Long-term data – import large pcap files, for hours, days, weeks, in real time.
- Created by a large number of trace tools (tcpdump, Tshark).
- Auto-Analysis – analyze thousands of data automatically using Deep Packet Expert Profiles
- Incidents – Create incidents based on variable thresholds per object
- Long-Term Perspective – Visualize incidents and raw files in intelligent dashboards, over hours, days, weeks or months
- Incident Correlation – Importing incidents into service management, these become part of the correlation framework
- Automation – the analysis, step by step

Benefits
- any know protocol or metrics field
- one tool for all level s
- critical states or incidents in my trace files
- Which category is affected (network, application, connection)
- which session/user is most affected
- are there security attacks or scans
- where do these come from?
- What exact metric caused the problem
- Which threshold values were exceeded and when
- Deep insights over a long period of time – for seconds, hours or days, weeks, months, year
